If you’ve recently downloaded Bitwarden as your go-to password manager, you might want to double check that it’s not masquerading as password-stealing malware. Proofpoint researchers identified a new malware they’re calling ZenRAT that’s prompting unsuspecting users to download fake installation packages of Bitwarden.
This malware seems to only be affecting Windows users, while users on other platforms are only sent to a benign webpage. Proofpoint was tipped off to this malicious software by Jérôme Segura at Malwarebytes, but it’s unclear at the moment how people are stumbling across the malware in the first place.
How to avoid this password-stealing malware
If you’re not using Windows, you’re safe from this malware attack. Anyone using a different OS who clicks on the fake Bitwarden site is sent to a webpage containing a cloned article from opensource.com, but there’s no malware in sight.
For Windows users, clicking on the fake Bitwarden site opens up a page that looks almost identical to the real Bitwarden site. If you look at the address bar, however, you’d see that the site address reads bitwariden[.]com rather than the real bitwarden.com.
On this fake Bitwarden site, clicking the Download button or the Desktop installer for Windows Download button would send a request to crazygameis[.]com to grab the malicious Bitwarden installation package. Proofpoint notes that crazygameis[.]com no longer appears to be hosting the malware, and the names and versions of the malware have changed a few times over the past few months.
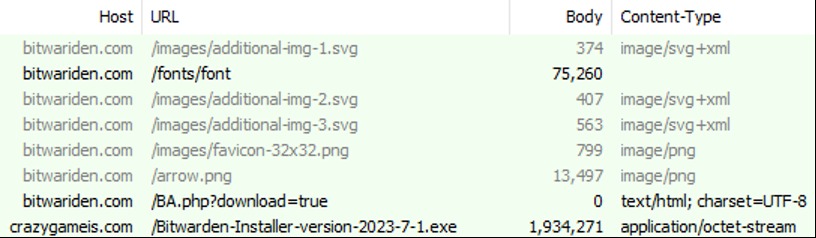
Only Windows users can access this fake Bitwarden site, but links for Linux and macOS downloads are still clickable. If someone clicks on a non-Windows download link, they’re redirected to the actual Bitwarden site.
When Proofpoint looked at the installer details for the malware package, they found the installer posing as Speccy, a software used to gather system specifications, and claiming to be signed by Tim Kosse, known for developing the Filezilla FTP/SFTP software.
According to Proofpoint, “The installer file copies itself to C:\Users\[username]\Appdata\Local\Temp, and creates a hidden file, named .cmd in the same directory that launches a self-deletion loop for both itself, and the installer file.” This self-deletion loop means that the file will automatically remove both it and the installer as soon as it finishes running.
It looks like ZenRAT is collecting host data once it’s installed, including your computer’s CPU Name, GPU Name, OS Version, installed RAM, IP address and gateway, installed antivirus programs, and installed applications.
Right now, Proofpoint doesn’t have any leads on how traffic is being directed to the fake Bitwarden site in the first place. Historically, fake software installers catch victims through SEO Poisoning, adware bundles, or email phishing.
SEO Poisoining, or phishing through fake sites and ads in search engine results, seems to be growing in popularity, so be extra careful to read the site’s address before clicking on it, downloading anything, or inputting personal information. For extra security in the future, be sure to check out these Windows security settings you should change.
Back to Ultrabook Laptops
Source link
 notebook.co.id informasi dan review notebook laptop tablet dan pc
notebook.co.id informasi dan review notebook laptop tablet dan pc