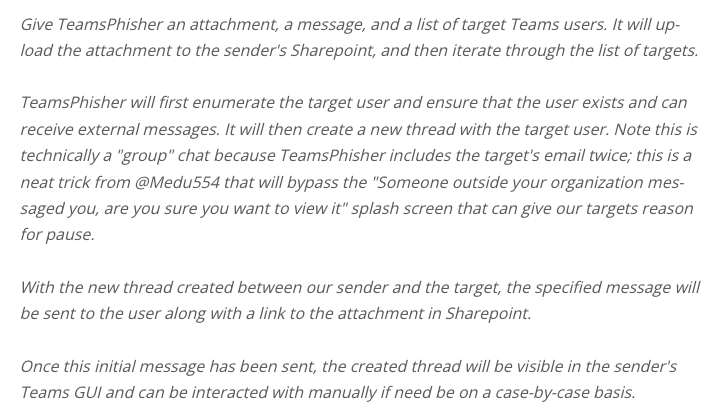
According to a report on Neowin, a member of the US Navy exploited a flaw in Microsoft Teams’ code. Hypothetically it could be used by hackers to send malicious attachments to a Teams group from an outside source.
Alex Reid, a member of the US Navy’s Red Team (a cybersecurity team within the Navy), published the “TeamsPhisher” tool on GitHub. The Red Team’s stated purpose is to simulate hacker attacks and then create solutions to use in defense against these hacker attacks.
How to protect against this Microsoft Teams exploit
According to the README file on GitHub, businesses using Teams can circumvent exploits like the TeamsPhisher and block it from accessing user meetings” by managing the options related to external access via the Microsoft Teams admin center under Users -> External access.” Teams admins can set up a “universal block as well as allowing only specific external tenants for communications.”
For its part, a Microsoft spokesperson responded to Bleeping Computer, stating that they were aware of the report, but noted the exploit relies on social engineering to be successful. Then Microsoft encouraged its users “to practice good computing habits online, including exercising caution when clicking on links to web pages, opening unknown files, or accepting file transfers.”
To me, it sounds like Microsoft doesn’t see this as a major issue, and that it is up to users of Microsoft Teams to police themselves and not accept or open files or links of unknown origins.
This is good basic advice for any time you’re using the internet, but it seems a little dismissive in the grand scheme of things because it’s been proven by the US Navy your product is broken and needs to be fixed.
Source link
 notebook.co.id informasi dan review notebook laptop tablet dan pc
notebook.co.id informasi dan review notebook laptop tablet dan pc