Thanks to a report in TheHackerNews, we know that Microsoft Word documents are being used to exploit known remote code execution flaws. The flaws are used as phishing lures to sneak the LokiBot malware onto compromised computers.
These so-called “LokiBots, ” also known as Loki PWS, have stolen users’ information since 2015 and remain a well-known trojan. Cara Lin, a security researcher with Fortinet FortiGuard, said, “It primarily targets Windows systems and aims to gather sensitive information from infected machines.”
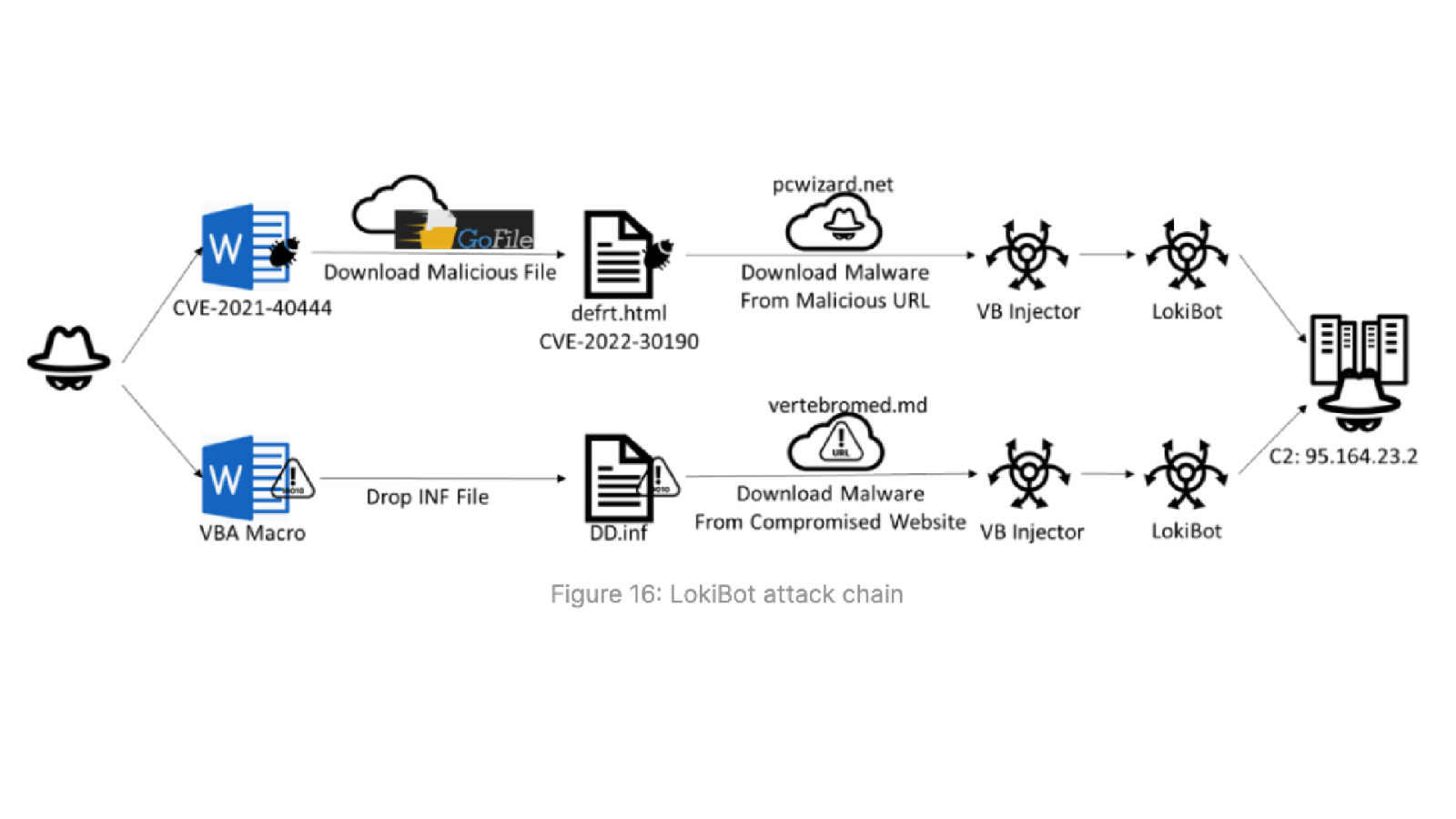
Fortinet first noticed the attack campaign in May 2023; the company released a statement saying the attacks take advantage of CVE-2021-40444 and CVE-2022-30190 (aka Follina) to achieve code execution.
How it’s done
According to the folks at Fortinet, the Word file that activates CVE-2021-40444 uses an external GoFile link that’s embedded within an XML file which leads to the download of an HTML file that exploits Follina to download a next-stage payload, an injector module written in Visual Basic that decrypts and launches LokiBot.
On top of all this, and not to add to your worry, the injector also uses evasion techniques to check your system for the presence of debuggers and determine if it’s running in a virtualized environment. So this malware is super smart and invasive.
Discovered towards the end of May, an alternative chain starts with a Word document incorporating a VBA script which then executes a macro immediately when users open the document using the “Auto_Open” and “Document_Open” functions.
This macro script subsequently delivers a payload from a remote server, which also functions as a way to load LokiBot and connect to a command-and-control (C2) server.
LokiBot’s, yes there are several
This is not the first LokiBot or the last. Like the deity of mischief, who can conjure up multiple versions of themself, there appear to be many variants that affect every OS imaginable. This current one is not confused with the LokiBot, a known Android banking trojan that can log your keystrokes, capture screenshots and gather your login information. That filthy trickster will siphon your financials, especially your cryptocurrency.
Cara Lin from Fortinet states, “LokiBot is a long-standing and widespread malware active for many years,” Lin said. “Its functionalities have matured over time, making it easy for cybercriminals to use it to steal sensitive data from victims. The attackers behind LokiBot continually update their initial access methods, allowing their malware campaign to find more efficient ways to spread and infect systems.”
So please remember to remain diligent about not opening suspicious emails, and do not open Word documents from email addresses you do not recognize. Also, you should look at our best antivirus page to see if you can increase your security level.
Source link
 notebook.co.id informasi dan review notebook laptop tablet dan pc
notebook.co.id informasi dan review notebook laptop tablet dan pc